Address Resolution Protocol (ARP) is one of the most important network layer protocols in the OSI model that assists in determining the MAC (Media Access Control) address given the system’s IP address, i.e. the main duty of the ARP is to convert the 32-bit IP address (for IPv4) to 48-bit address, i.e. the MAC address.
How does ARP function?
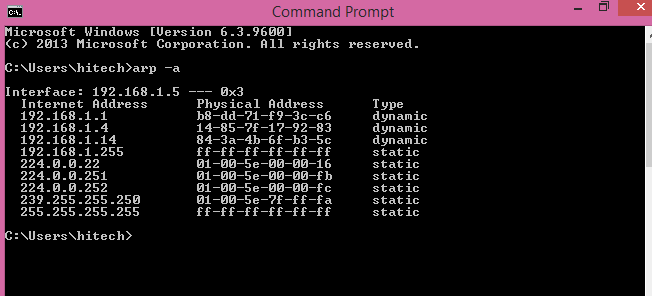
When the source wants to find out the MAC address of the destination device at the network layer, it first looks for the MAC address (Physical Address) in the ARP cache or ARP table. If it is present, it will communicate using the MAC address from there. If you want to view your ARP cache in Windows, open Command Prompt and type command —’arp -a’. This is an example of an ARP table.
- The source device will generate an ARP Request message if the MAC address is not found in the ARP table. The source includes its own MAC address, IP address, and destination IP address in the request message, and the destination MAC address is left blank because the source is looking for it.
Sender’s MAC Address 00-11-0a-78-45-AD
Sender’s IP Address 192.16.10.104
Target’s MAC Address 00-00-00-00-00-00
Target’s IP Address 192.16.20.204
- The ARP request message will be broadcast to the local network by the source device.
- All other devices in the LAN network receive the broadcast message. Now, each device will compare the destination’s IP address to its own. If the destination’s IP address matches the device’s IP address, the device will send an ARP Reply message. If the IP addresses do not match, the packet is simply dropped by the device.
- The device whose IP address in the packet matches the destination IP address will respond and send the ARP Reply message. This device’s MAC address is contained in this ARP Reply message. Because it will need to contact the source soon, the destination device updates its ARP table and stores the source’s MAC address. This device’s source is now the destination (target), and the ARP Reply message is sent.
Sender’s MAC Address 00-11-0a-78-45-AA
Sender’s IP Address 192.16.20.204
Target’s MAC Address 00-11-0a-78-45-AD
Target’s IP Address 192.16.10.104
- The ARP reply message is unicast and is not broadcasted because the source device that is sending the ARP reply to the destination knows the source device’s MAC address.
- When the source receives the ARP response, it learns about the destination MAC address and updates its ARP cache. The packets can now be sent because the source MAC address has been changed to the destination MAC address.
- Frame 1: 60 bytes on wire (480 bits), 60 bytes captured (480 bits)
- Ethernet II, Src: Universa_6c:Oc:cc (00:1a:61o:6c:0c:cc), Dst: Broadcast (ff:ff:ff:ff:ff:ff)
- Address Resolution Protocol (request)
- Hardware type: Ethernet (1)
- Protocol type: IPv4 (0x0800)
- Hardware size: 6 Protocol size: 4
- Opcode: request (1)
- Sender MAC address: Universa_6c:Oc:cc (00:1a:61):6c:Oc:cc) Sender IP address: 10.10.10.2
- Target MAC address: 06:00:80 00:00:06 (00:00:00:00:00:00)
- Target IP address: 10.10.10.1
- An example of an ARP Reply message captured. The MAC address requested by the source is included in the reply message. The ARP Reply message contains the MAC address 00:1d:09:f0:92:ab.
- Frame 2: 42 bytes on wire (336 bits), 42 bytes captured (336 bits)
- Ethernet II, Src: Dell f0:92:ab (00:1d:09:f0:92:ab), Dst: Universa_6c:Oc:cc (00:18:6b:6c:0c:cc)
- Address Resolution Protocol (reply)
- Hardware type: Ethernet (1)
- Protocol type: IPv4 (0x0800)
- Hardware size: 6
- Protocol size: 4
- Opcode: reply (2)
- Sender MAC address: Dell_f0:92:ab (00:1d:09:f0:92:ab) Sender IP address: 10.10.10.1
- Target MAC address: Universa_6c:Oc:cc (00:18:6b:6c:0c:cc) Target IP address: 10.10.10.2.
The Benefits of Using ARP
- If we know the IP address, we can easily determine the MAC address.
- End nodes are not required to “know” MAC addresses. They are available when needed.
The Drawbacks of Using ARP
ARP attacks such as ARP spoofing and ARP Denial of Service are possible. ARP Spoofing is a technique that allows an attacker to attack an Ethernet Network, which may result in the sniffing of data frames on a switched Local Area Network or the attacker stopping traffic entirely, also known as ARP denial of Services.
